Identity firewall IDFW enables one to configure distributed firewall rules based on Active Directory user group.
Identity firewall can be utilized for virtual desktops, remote desktop sessions RDSH and also for physical machines.
VMware NSX will control access to the target/destination servers based on the user logged in to the source VM. In this case, IDFW processing is done at the source.
Identity firewall rule is configured based on Active Directory user group.
IDFW must know which virtual desktop an Active Directory user logs onto in order to apply firewall rules.
There are two methods for logon detection:
Guest Introspection (GI) and/or
Event log scraping.
With RDSH, administrators create security groups with different users in Active Directory (AD), and allow or deny those users access to an application server based on their role. For example, Application Team and Database Team can connect to the same RDSH server, and have access to their own set of applications from that RDSH server.
Identity firewall supported configurations are documented here.
IDFW workflow:
1. Enable NSX File Introspection driver and NSX Network Introspection driver (VMware Tools full installation adds these by default).
2. Enable Identity firewall on DFW

3. Configure Identity firewall active directory
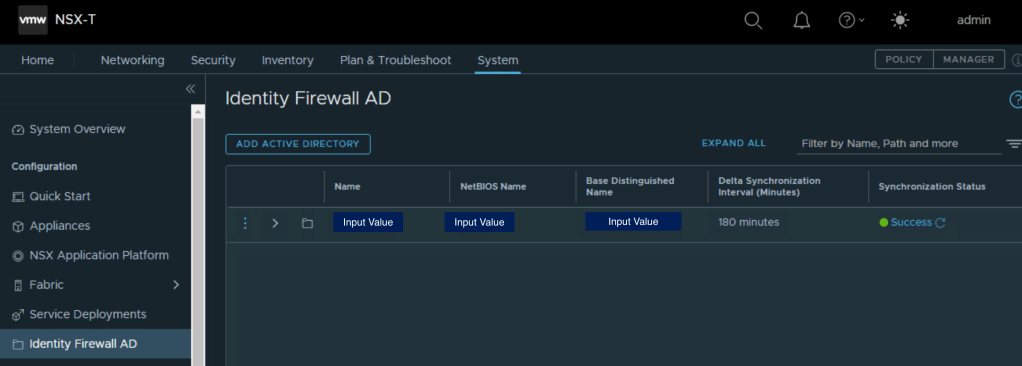
4. Synchronize Active Directory
Selective sync allows you to selectively choose organizational units for sync. Only the selected organization units which are created and changed since the last delta sync will be updated during a selective sync.

5. Create a group named ‘NSX’ with Active Directory Group members

5. Create a dynamic security group ‘Web’ based on VM name as a criteria

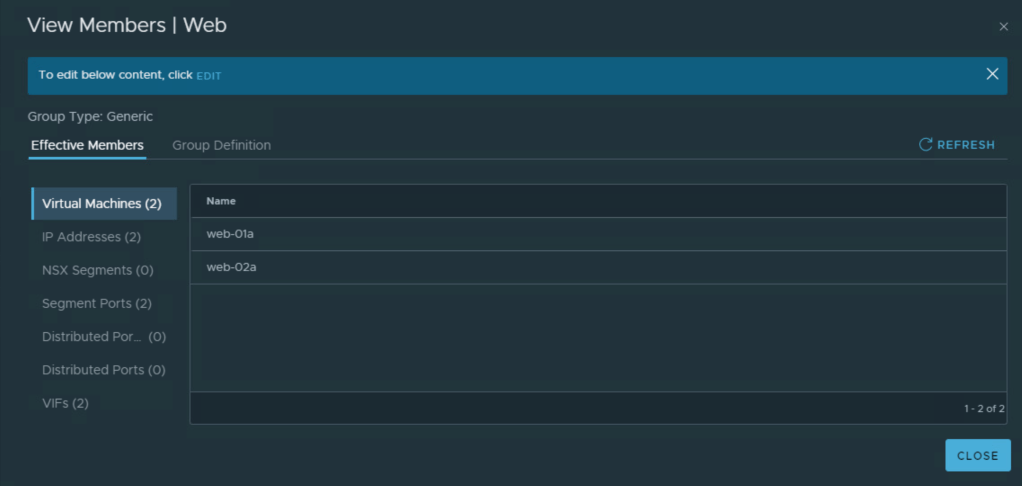
6. Create firewall rule under NSX DFW

Notice that the first firewall rule is being applied to the VM where user logs in. ‘Applied To’ field is important here. This firewall rule is not being applied to members of the group ‘Web’. Remember IDFW user context is processed at the source.
Validation:
I will log into a virtual desktop using my AD user which is a member of the AD group ‘NSXGroup’ and open web pages of Web servers

I will also assign log label to the firewall rule to ensure that initiated traffic does hit the IDFW rule.


