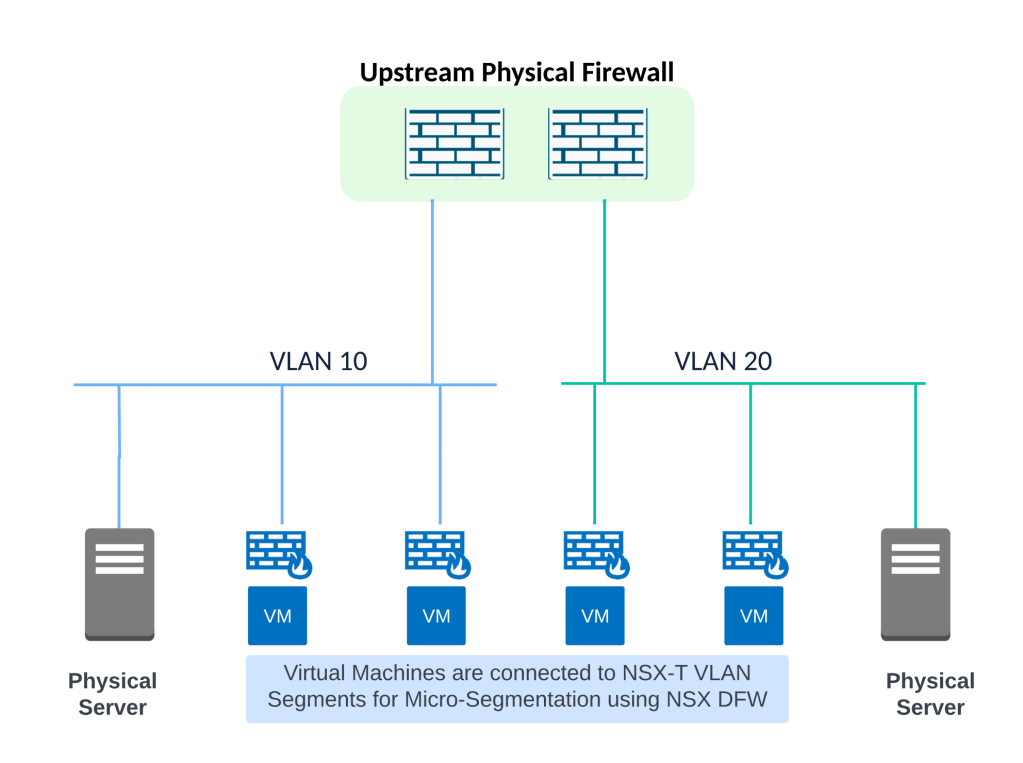
Why VMware NSX?
VMware NSX is L2 to L7 network virtualization and advanced security platform. NSX overlay networks which are backed by Geneve overlay protocol provide software defined networking capabilities. Overlay networking allows cloud scale networking whereby multiple overlay networks (NSX overlay segments backed by NSX overlay transport zone) related to multiple tenants can be provisioned using the same physical underlay networking infrastructure; as compared to limited number of VLANs in the case of legacy physical networks.
Features such as Distributed Routing provide optimal traffic forwarding and avoid traffic hair pinning to centralized, physical devices such as physical router, physical firewall. Distributed routing is done by the Distributed Router (DR) running as a kernel module in each hypervisor. Distributed routing provides inter-subnet routing between VMs on the same ESXi server and connected to different NSX overlay networks; and such traffic does not leave the hypervisor at all. Such traffic is processed completely within the server and does not have to leave the server to traverse multiple layer 2 physical switches before reaching gateway. In the case of NSX overlay networking, distributed router (gateway) is instantiated locally on each ESXi server.
By deploying NSX edges, services such as Gateway Firewall, NAT, VPN, DHCP can be consumed.
VMware NSX integrates well with VMware vSphere and any network created by NSX Manager is auto-created on appropriate VDS of the vCenter server. And then these networks can be consumed by connecting such networks to appropriate virtual machines.
VMware NSX offers distributed firewall capabilities which means that you can program firewall rules on vnic level of a virtual machine. Communication between virtual machines in the same subnet isn’t allowed unless explicitly allowed by NSX distributed firewall rule. In addition to this, advanced security features such as Distributed IDS/IPS, Distributed Malware prevention, NSX Gateway firewall, TLS inspection, URL filtering, FQDN analysis, IDS/IPS on NSX gateway firewall, Malware prevention on NSX gateway firewall, NSX Network Detection & Response are also available in VMware NSX.
In this post, we will explore how virtual machines can be secured by using NSX Distributed Firewall and how traditional VLAN backed networks can be migrated to NSX overlay networking.
High level approach involves firstly securing the virtual machines using NSX DFW and then once all the virtual machines in a given IP subnet are secured, then gateway migration can be done for that particular subnet, destination/target network for the virtual machines being NSX overlay segment.
Inventory of all applications and all IP endpoints needs to be in place:
- Which virtual machines belong to which application?
- Are there physical servers and virtual machines in the same IP subnet?
Migration approach # 1:
One potential migration approach involves moving physical servers to new IP subnets which are dedicated to physical servers only. See figure below.
This will need re-IP of physical servers whereby new IP addresses are allocated to physical servers.
Next deploy VMware Aria Operations for Networks for planning micro-segmentation.
Based on the inventory collected earlier, define application in VMware Aria Operations for Networks.
VMware Aria Operations for Networks will provide recommended NSX Distributed firewall rules for the configured application which will then be configured on NSX Distributed Firewall.
Applications will be secured on a application by application basis.
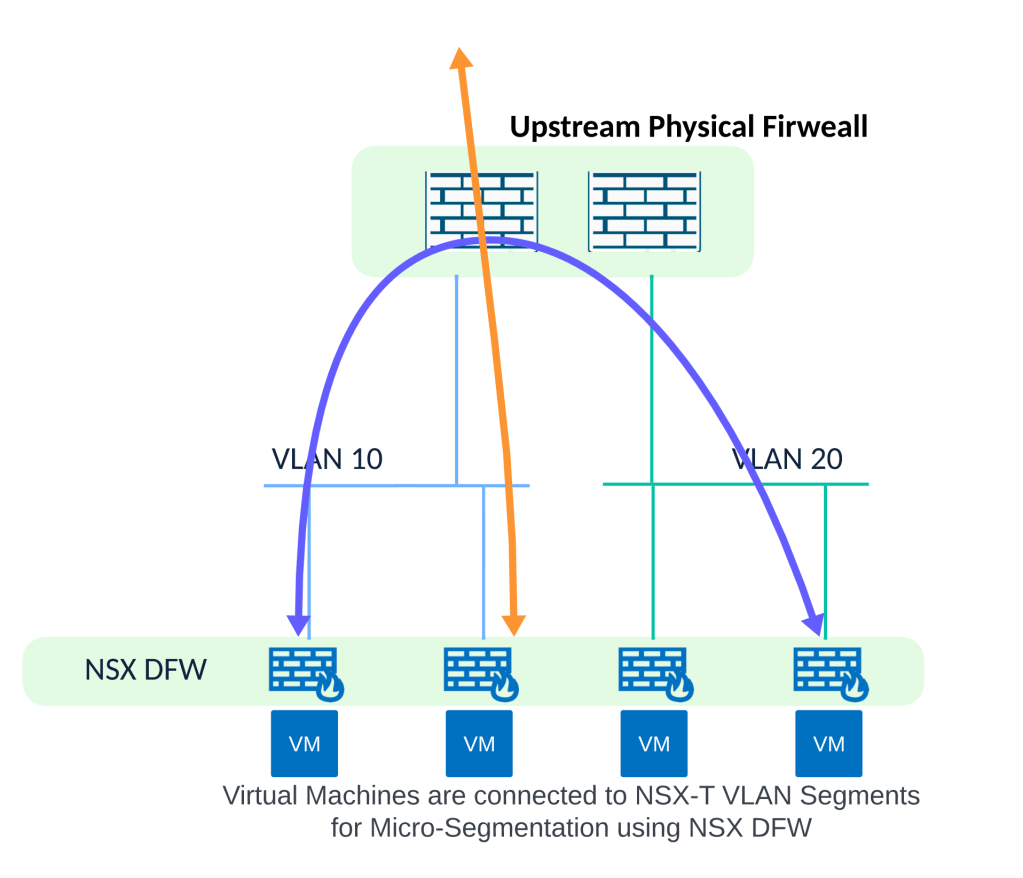
NSX DFW firewall policy for application x (collection of firewall rules) will have the ‘allow’ firewall rules for application x followed by a ‘catch all’ rule for application x. This ‘catch all’ firewall rule will have action as ‘allow’ when the firewall rules for application x are being configured, to be modified to ‘drop’ during a maintenance window. This ‘catch all’ DFW rule for application x will be applied only to virtual machines belonging to application x. This can be controlled by ‘Applied To’ field of NSX DFW rule.
Default rule, catch all rule on NSX DFW will be allow until all applications are secured by NSX Distributed Firewall. Once all applications are secured by NSX DFW then the default rule on NSX DFW can be modified to ‘block’.
Next in a maintenance window, perform these actions for the application virtual machines:
- Change VM network from Distributed Port Group to NSX VLAN Segment (create NSX VLAN segment using the same VLAN ID as that of Distributed Port Group)
- Ensure that last DFW rule in the firewall policy of application x has action has ‘drop’ instead of ‘allow’ and this firewall rule is only applied to virtual machines of application x.
Topology will look like below:
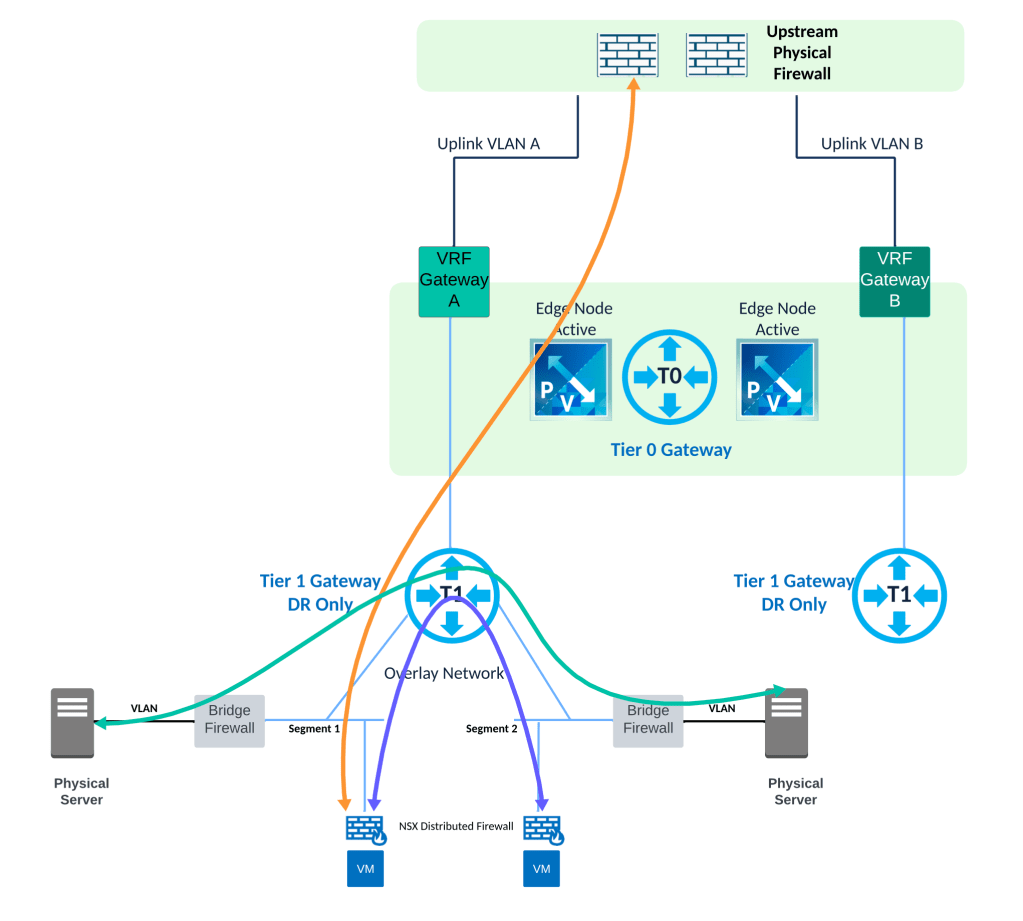
Build required NSX-T topology, sample topology is shown below using VRF gateways and Tier 1 Gateways.
Next, we are ready to move gateway from VLAN backed gateway to NSX overlay backed gateway on appropriate NSX Tier 1 Gateway. Refer topology below.
Appropriate firewall rules need to be in place on the physical firewall to allow north-south traffic in and out of the software defined data center SDDC.
Overall migration approach is outlined below
Migration approach # 2
In this approach, L2 adjacency is required between physical servers and virtual machines in the same IP subnet. Hence NSX L2 bridging will be configured.
High level approach will be the same, first secure virtual machines using NSX DFW and then migrate gateway to NSX Tier 1 Gateway.
VMware Aria Operations for Networks will be deployed for planning micro-segmentation.
Appropriate NSX DFW firewall rules will be configured on NSX DFW based on firewall rule recommendations provided by VMware Aria Operations for Networks.
In a maintenance window, all VMs for application x will be secured by NSX DFW. For this the virtual machine network needs to change from Distributed Port Group to NSX VLAN segment. Also the ‘catch all’ rule for application x needs to have action as ‘drop’ instead of allow. This ‘catch all’ rule for application x will only be applied to virtual machines of application x by using ‘Applied To’ field of NSX DFW rule. This rule is for the virtual machines of application x and this is not the default rule on NSX DFW. The default rule on NSX DFW can have action as ‘drop’ once all virtual machines are secured by NSX DFW.
Configure L2 bridging on NSX as shown in diagram below and ensure NSX-T configurations for NSX gateways are already in place.
Next bridge firewall rules will be configured to secure physical server to physical server communication as highlighted below. These rules will mimic the inter-subnet firewall rules on upstream physical firewall for physical servers.
Overall migration approach is outlined below.